FluBot, a mobile phone scam that spread throughout the world via fake text messages, has been busted down by police in 11 nations.
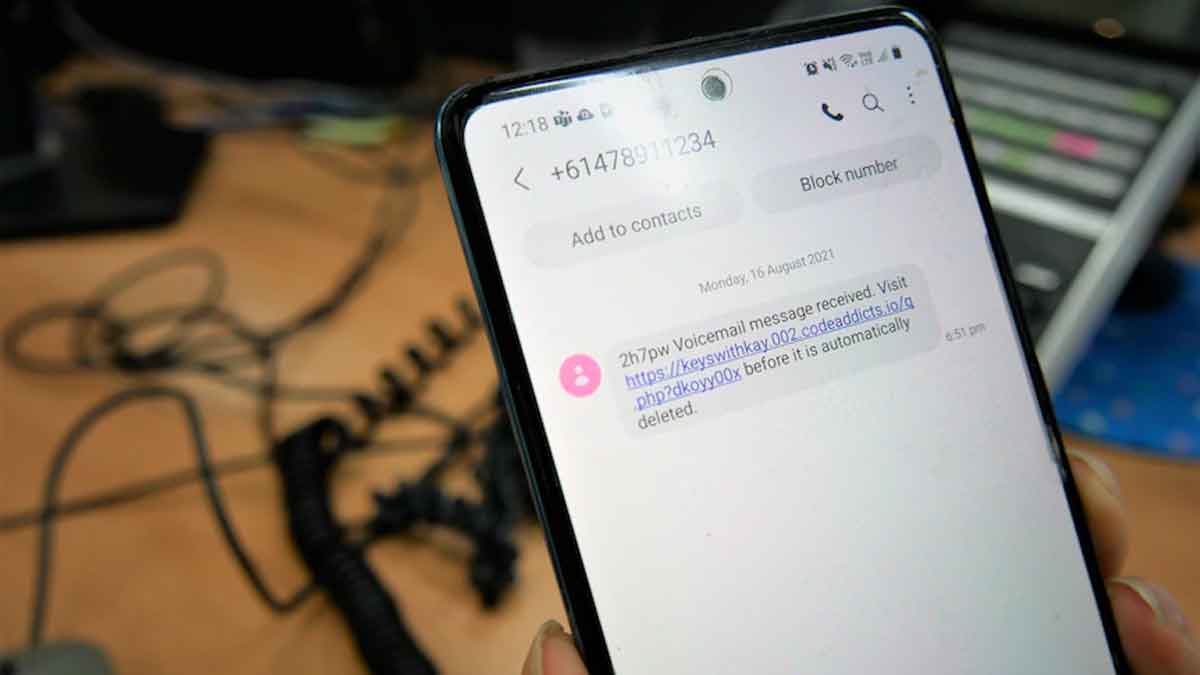
In May, Dutch cybercops spearheaded an operation to combat the spyware, which infects Android phones via messages claiming to be from a delivery company or claiming that a person has a voicemail waiting.
Hackers would then take bank account information from infected phones, which would subsequently send messages to other phones in the user’s contact list, thereby spreading the scam like a flu virus.
“To date, we have separated ten thousand victims from the FluBot network and averted approximately 6.5 million spam SMS messages,” according to a statement from Dutch police.
FluBot was one of “the fastest-spreading mobile malware to date,” according to Europol, and was “capable of spreading like wildfire due to its capacity to access an infected smartphone’s contacts.”
Read more: Binance joins hands with Pakistan for busting $100 million crypto scam
The software had been rendered “inactive,” but police are still on the lookout for the perpetrators, according to the report.
“Law enforcement now has control of this FluBot infrastructure, putting an end to the dangerous cycle,” Europol stated.
Australia, the United States, Belgium, Finland, Hungary, Ireland, Romania, Spain, Sweden, Switzerland, and the Netherlands were among the countries involved in the investigation, which was managed by Europol’s cybercrime centre.
After initially appearing in December 2020, FluBot became one of the world’s most prominent cyberscams, “wreaking havoc” around the world, according to Europol.
The malware has infected a “large number of devices worldwide,” notably in Europe and the United States, with “significant incidents” in Spain and Finland, according to the agency.
Last year, Australian media reported that FluBot was spreading “like a tsunami,” with some users receiving a barrage of texts.
FluBot Method
Officials claim they don’t want criminals to know how they cracked the fraud, therefore details on how authorities uncovered it is not available.
According to Europol and the Dutch authorities, FluBot’s method was straightforward.
It would arrive “mostly via a fake SMS purporting to be from a well-known parcel delivery service” or a message informing the user that they had a voicemail to listen to.
They’d then be invited to either click on a link to download a parcel tracking app from the parcel service or listen to voicemail.
FluBot, on the other hand, would install malware on their phones. The bogus software would then request permission to access a variety of other apps.
According to Europol, hackers may observe their targets typing passwords for banking, credit card, or cryptocurrency apps and steal from them.
Its ability to access a phone’s contact information and then send bogus texts to other phones made it “extremely dangerous.”
“Many victims are unaware that they have been infected with malware. The infection continues to spread without the owner of a mobile phone noticing,” Dutch police say.
Only phones running Google’s Android operating system were targeted by the fraud. Apple’s iOS operating system remained unaffected.